Mobile phones are vital instruments in the digital age since they hold a plethora of personal data, such as private papers and precious memories. This ease, however, comes at a cost: the ongoing risk of cyberattacks. As fraudsters constantly modify their tactics, we must be more vigilant than ever about protecting our mobile devices.
Protecting our identities, wallets, and privacy is just as critical as keeping our electronics working correctly. In order to safeguard your smartphone from cyberattacks and provide you the flexibility to browse the internet with confidence and comfort, we’ll go over 10 crucial steps in this post.
Here is a guide to protect your phone from Cyberattack
1. Update the apps and firmware
Updating the firmware and apps on your Android smartphone on a regular basis is like building cybersecurity around your digital stronghold. Critical security fixes that fix flaws that cybercriminals exploit are often included in these releases.
Maintaining an up-to-date gadget greatly lowers the likelihood of becoming a victim of new threats and exploits. To always keep your device safe, make it a practice to check for updates often and to turn on automatic updates whenever you can.
2. Employ Robust Authentication Techniques
Robust authentication is your first line of defence against illegal access to your iOS mobile phone. While using standard pass codes is a good place to start, adding biometric identification techniques like fingerprint or face recognition provides another level of protection.
Complicated pass codes strengthen the security of your smartphone even further, making it far more difficult for hackers to access. Use the sophisticated authentication features on your smartphone to increase security without compromising usability.
3. Install Trustworthy Antivirus Software
Effective security software is necessary for your mobile device, just as you wouldn’t leave your house alone. Installing reliable antivirus software from reliable sources guarantees that malware, spyware, and other dangerous software may be found and removed from your device.
Antivirus software does routine scans as a preventative step against any hazards that could be present in the digital environment. To fully secure your device, choose a high-end antivirus program with cutting-edge capabilities and real-time protection.
4. Use Caution When Downloading Apps
Sometimes the attraction of installing new applications causes us to become unaware of possible dangers. Use cautious in order to minimize the chance of installing dangerous malware. Choose official app shops alone, such as the Apple App Store or Google Play Store, where software is carefully vetted.
Examine user reviews and app permissions carefully before installing to determine the app’s validity and any possible security risks. To find and remove dubious apps before they endanger your device, take into account using app reputation services or mobile security technologies.
5. Protect Network Links
It’s critical to secure your network connections in this connected world. Wi-Fi connections that are encrypted are more secure against bad actors’ unwanted access and data interception. By avoiding unprotected public Wi-Fi networks, you may further lower your vulnerability to data breaches and man-in-the-middle attacks, protecting your private data.
Purchase a trustworthy virtual private network (VPN) service to guarantee safe connection and encrypt your internet data, particularly while using public Wi-Fi hotspots.
6. Watch Out for Phishing Attempts
Phishing is still one of the most common online dangers that affect mobile users. Cybercriminals often use misleading emails, texts, or websites to fool people into sending private information. Being cautious is essential; examine sender addresses, stay away from dubious connections, and never provide personal information to unreliable sources.

When in doubt, use other routes to confirm the communication’s legitimacy. To strengthen your defences against this ubiquitous danger, think about using anti-phishing software or browser extensions to identify and prevent phishing attempts in real-time.
7. Turn on the Find My Device function
A mobile device that is lost or stolen might be disastrous if it ends up in the wrong hands. In these kinds of situations, turning on the Find My Device function is a ray of hope. You can locate your device and remotely delete its data to stop unwanted access by turning on the tracking and remote wipe features.
This preventative action gives comfort in the event of possible security breaches. Learn about the functions and features of Find My Device on your device, and make sure it is set up and activated to protect your data and device to the fullest.
8. Put into practice two-factor authentication (2FA)
By asking users to provide two forms of identity before providing access to an account or device, two-factor authentication (2FA) offers an additional layer of protection. Even in the event that passwords are hacked, 2FA dramatically lowers the danger of unwanted access, whether it is via a biometric scan, authentication app, or text message code.
Accept this extra protection to strengthen your online safety. Whenever feasible, use hardware-based security keys or authentication tokens for two-factor authentication (2FA). These solutions provide better defence against account takeover and phishing attempts than more conventional approaches.
9. Make Regular Backups of Your Data
Having a current backup of your important data is like having a safety net in case of a cyberattack or gadget malfunction. You may guarantee that you can promptly recover from unanticipated disasters by regularly backing up your contacts, images, papers, and other important data to secure cloud storage or external devices.
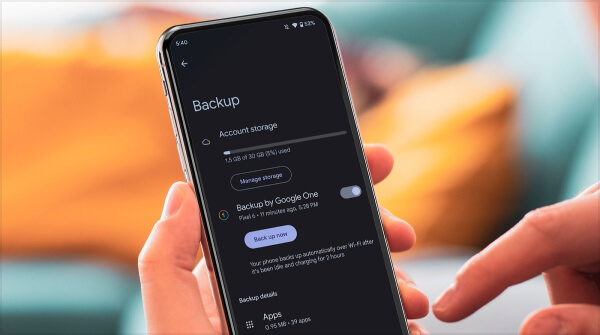
Consider data backup as a kind of protection against possible loss or compromise. Look into cloud storage companies or automatic backup programs that integrate easily with your smartphone to plan frequent backups and guarantee data safety without the need for human involvement.
10. Remain Educated and Informed
Because cyber risks are always changing, being aware is essential to protecting your mobile device. Use reliable sources to stay up to date on the most recent developments in cybersecurity, including new threats and best practices.
You may empower yourself to make wise judgments and confidently traverse the digital realm by familiarizing yourself with typical attack vectors and mitigation measures. Participate in online forums, go to cybersecurity seminars or webinars, and make use of the tools offered by governmental organizations and cybersecurity associations to expand your understanding and strengthen your defences against ever-evolving cyberthreats.
In summary
Mobile cyberattacks are a serious danger to our financial and personal security. However, you may greatly reduce these dangers and have a safer mobile experience by putting the ten preventative actions mentioned above into practice.
Every action you take to protect your phone from cyberattack—from routine updates and robust authentication to careful app installs and data backups—makes a significant difference. Remember that the best defences against cyber attacks for your digital assets are diligence and alertness. Remain vigilant, knowledgeable, and safe.

